You are leaving our Website
Using an external Link:
You are now leaving our website. The following page is operated by a third party. We accept no responsibility for the content, data protection, or security of the linked page..
URL:
Common Security Advisory Framework (CSAF)
The standard for structured Security Advisories
Vulnerabilities in hardware and software are a constant reality. Once systems reach a certain level of complexity, errors can no longer be avoided – and many of these errors can become security vulnerabilities that attackers exploit. Such security vulnerabilities are like open wounds in a company's digital infrastructure: they must be identified, understood, and addressed or at least treated as quickly as possible to prevent greater damage.
A central solution to this challenge is CSAF (Common Security Advisory Framework) – an open, standardized format for publishing and automatically exchanging machine-readable security advisories and vulnerability information. Developed as an open-source initiative, CSAF significantly simplifies and accelerates communication about security vulnerabilities and corresponding countermeasures.
By using CSAF, the manual effort in searching and evaluating security information can be significantly reduced. The framework enables manufacturers, system operators, administrators, and users to automatically collect and analyze information on known vulnerabilities - and determine if their products are affected. Even the confirmation of not being affected can be efficiently communicated through the Vulnerability Exploitability eXchange (VEX) profile within CSAF.
In an increasingly interconnected and complex digital world, the number of security-related vulnerabilities will continue to increase. Therefore, a modern vulnerability management based on CSAF documents will be indispensable in the future.

Join OASIS Open and qSkills™ for an intensive CSAF Week combining technical training with community exchange, designed to accelerate your organization's journey toward automated vulnerability management. Master the standard in three days of practical CSAF Workshops (Monday–Wednesday). Then join industry leaders at the CSAF Community Days (Thursday–Friday) to share insights, discover implementations, discuss the future of automated vulnerability management and connect with the global CSAF community.
CSAF Community Days | 13.-14.11.2025
Get informed and register now!
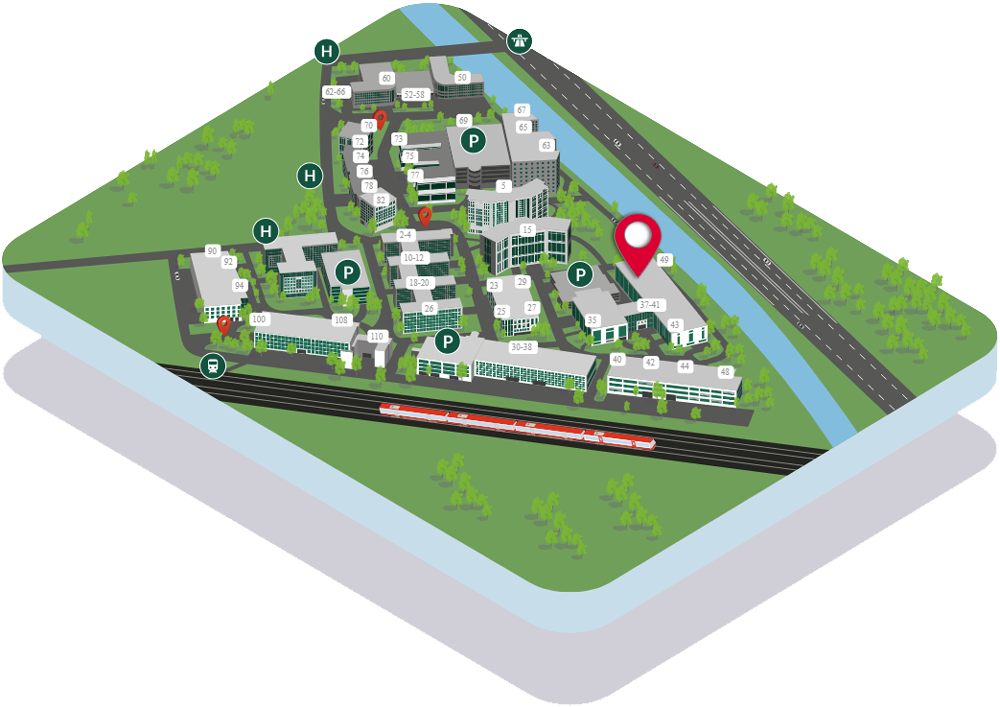
On 13th and 14th November 2025, the CSAF Community Days will take place at the Südwestpark – Forum in Nuremberg. This onsite event is aimed at developers, practitioners, manufacturers, users, and anyone involved with the Common Security Advisory Framework (CSAF). Discussions will focus on best practices, tools, success stories, and innovations related to CSAF.
Location:
Südwestpark – Forum
Südwestpark 37–41
90449 Nuremberg
Germany
Program CSAF Community Day 1
November 13, 2025
Welcome & Opening Remarks
The Hidden Cost of CVEs: Can CSAF and VEX Change the Equation?
Lisa Olson (Microsoft™)
Every time Microsoft™ publishes a CVE, thousands of security professionals worldwide spring into action - analyzing, prioritizing, and responding. These efforts, while essential, represent a significant global investment of time and resources. As regulatory frameworks like the CRA push for greater transparency, Microsoft™ is committed to delivering vulnerability information that is both comprehensive and actionable. But does more transparency always mean more efficiency? In this session, we’ll explore the true cost of CVEs in terms of man-hours and examine whether machine-readable standards like CSAF and VEX can help reduce this burden for stakeholders across the ecosystem.
One Year of CSAF - Lessons, Statistics, and Impact
Jacco Ligthart (NCSC-NL)
One year ago, we were surprised to learn that we had become the largest producer of CSAF (Common Security Advisory Framework) documents. That milestone sparked a focused effort to not just maintain volume, but to significantly improve the quality, consistency, and usefulness of the data we publish. Over the past year, we’ve refined our CSAF generation processes, improved adherence to the standard, and enhanced the structure and accuracy of our vulnerability data and advisories. In this presentation, I’ll share detailed statistics and graphs that illustrate how our approach has evolved. Beyond internal improvements, I’ll highlight several real-world stories of how others are consuming and integrating our CSAF data. This session is aimed at others who are producing or working with CSAF documents and are looking to scale, improve their processes, or simply learn from another organization’s journey. Whether you’re deep into CSAF adoption or just starting out, I hope our insights will help inform your path forward.
Networking Break with Morning Tea
An easy Way to become a CSAF Provider with Github Actions
Bernhard Reiter (Intevation GmbH)
A demonstration of how to use the csaf-tools GitHub Action to publish security advisories from a repository to the static web hosting of the platform.
This is the easiest way to become a CSAF trusted provider. Useful for software products that use GitHub Pages and want to store their CSAF documents in the repository.
The necessary signing can be done before uploading a document or with an OpenPGPv4 key saved as GitHub secret.
The GitHub Action is developed in autumn 2025 and uses the Free Software tool csaf_provider to build a directory of static contents. That can be served via HTTP.
Looking at the structure of this solution, you will learn the basic of how csaf_provider works and what principal steps are necessary to do a similar integration for a different continuous deployment system.
Lessons Learned from Automating the CSAF Publication Flow
Jan Thielscher (EACG)
Jan will dive into the challenge of automating the publication flow of CSAF documents and how to overcome them. Based on the idea to automatically create CSAF documents - whether VEX, Security Advisory or Informational Advisory - initiated from the vulnerability notification, this speech will outline the information required to achieve this goal. The talk will present and briefly discuss solution designs and describe the finally implemented solution. A short demonstration will show, how the result looks like and report from user reactions. Finally, remaining challenges and thoughts on further improvements concerning publication and collection of CSAF documents will be presented. This comprises thoughts on reducing the data load required to be shared/processed in the given design approach.
Challenge your Checker with Contravider: Better Testing for CSAF Distribution Tools
Sascha L. Teichmann (Intevation GmbH)
The CSAF standard defines rules for the automated distribution of advisories and VEX documents. Meeting these rules is complex, as unattended discovery and retrieval require strict conformance. To prepare for version 2.1, we have developed a test suite called contravider. It acts as a deliberately faulty provider. By breaking selected requirements, it can produce negative test cases that help validate implementations under error conditions. We present the design and use of this tool. Our approach builds test configurations with Git change sets applied to a compliant reference data set. This enables reproducible and extensible testing.
Lunch
BOMnipotent - Server and Client for SBOMs and CSAF Docs
Simon Heidrich (Weichwerke Heidrich Software)
BOMnipotent is a server-client application pair for managing supply chain security documents, specifically SBOMs and CSAF documents. It contains an access management system based on roles and TLP labels, and acts as a CSAF Trusted Provider. The development focus is on security, reliability and ease of use. The client is free to use, but fully operating the server requires a paid subscription for commercial entities. For non-commercial entities, BOMnipotent is completely free in all its facets.
Implementing a CSAF SBOM Matching System - Standard vs. Reality
Christian Banse (Fraunhofer™ AISEC)
This walk will give insights into implementing a CSAF SBOM matching system and the challenges encountered when trying to implement the standard in the real world. Contracted by the German BSI™, Fraunhofer™ AISEC has implemented CSAF support in the popular dependency management system, DependencyTrack. CSAF’s SBOM matching model aims to precisely map advisory scope to actual products and versions in an environment, using structured product identifiers and matching rules. In practice, successful implementation requires reliable canonical identifiers (CPE, PURL, etc.), consistent versioning, and normalized product naming across toolchains. Fraunhofer™ AISEC’s work in DependencyTrack shows how automation can ingest CSAF feeds and apply matching logic to a project’s bill-of-materials, surfacing relevant advisories automatically.
Bringing together SBOMs and Advisories, with GUAC Trustify
Jens Reimann (Red Hat)
If you already have sources for SBOMs and advisories, great. You are creating them yourself or have them available from other sources, awesome. But now what? Let’s bring them together and get an overview on the status of your SBOM. This talk will give a quick introduction on GUAC Trustify, explain how data gets into the system, and how you can leverage it to gain some insight. We will see what the system has to offer when it comes to bringing ready-made SBOMs and advisories together. How you can inspect the information, and see the correlation between content and of SBOMs and mapped to advisory information. Additionally, we will also take a brief look at how we, at Red Hat, use this system in the whole software creation process. And of course, there will be some room to talk about the bad and the ugly, and what we can do to improve the situation.
Networking Break with Afternoon Tea
CSAF Extension - The best worst idea?
Thomas Schmidt (BSI™)
This session given an overview of the concept of CSAF extensions. It will cover the history, challenges and perspectives from different use cases. It will lay down the intended scope and rules for CSAF extensions and provide examples.
Lightning Talks
various Speaker from the CSAF Community
This session provides the opportunity for on-site participants to share their knowledge in a short presentation. Sign-up at the event only.
Day 1 Wrap Up
Social Event
Program CSAF Community Day 2
November 14, 2025
Welcome and Day 1 Recap
Security Advisories - Facts, Fashions, and Fiction
Stefan Hagen (CSAF TC)
The talk presents and applies observations from two decades of unpaid standardization and software development to promote future interoperability in information exchange. A brief overview of the journey through the eras of XML and JSON monoculture offers a retrospective assessment of perceived gains and losses. Short visits are made to projects that offer models of general information in addition to specific data format recipes, thus staying closer to the actual needs, similar to a domain-driven design method. The reality of voluntary efforts in collaboration with paid partners, as well as old and new trends — from passivity to interpolating hallucinations — are illustrated in the resulting travel images. Small excursions into neighboring problem areas — such as behavioral or provenance analysis — are undertaken to explore how the merging and adaptation of related concerns can be promoted without dissolving the core positions of the security recommendations. The assumed position of current standardization is presented in dystopian colors, yet some of the foreseeable future paths promise less misleading fiction and more exciting facts for the common good.
Bringing Trusted Vulnerability Reporting to Every Organization with DevGuard
Patrick Rissmann (l3montree)
DevGuard is an open-source tool developed by L3montree GmbH that enhances the security of the software development process by helping organizations manage dependency vulnerabilities, first-party code weaknesses, and license compliance issues. Until recently, DevGuard relied on basic VEX files to exchange vulnerability information — an effective yet limited approach in terms of flexibility and expressiveness. To address this, we introduced CSAF (Common Security Advisory Framework) support into DevGuard. The goal: enable every organization and project using DevGuard to automatically generate and directly publish CSAF-conformant reports based on their stored vulnerability data. In this model, each organization effectively becomes a trusted CSAF provider, able to communicate vulnerability assessments in a standardized and interoperable way. This presentation outlines the full journey — from analyzing the CSAF specification to designing and implementing the feature in Go. It will cover technical and conceptual challenges. A live example will be presented using the openCode platform of ZenDiS, where DevGuard operates as a platform service. Here, every openCode project can automatically publish CSAF and VEX documents, backed by enterprise-grade functionality such as SBOM import, integration with ticket management systems, and vulnerability assessment workflows. The session will conclude with a roadmap and vision for collaborative vulnerability management — leveraging CSAF and VEX to enable crowdsourcing of vulnerability assessments, sharing results within and across organizations, and strengthening the open-source ecosystem through transparency and automation. By bridging DevGuard’s open-source foundations with CSAF’s trusted reporting capabilities, this work demonstrates how standardized vulnerability communication can become a natural part of modern, scalable software security management.
Networking Break with Morning Tea
An Architecture for Matching CSAF Documents on Industrial Asset Inventories
Daniel Rittershofer (Fraunhofer™ IOSB)
We present BSI™’s project 625 on CSAF matching in industrial environments. The aim of the project is to match an industrial asset inventory with a CSAF document database so that operators can efficiently identify relevant security advisories for the assets contained in their plants. We present our system architecture and implementation as well as our approach to matching CSAF documents to device and software asset information. The open-source asset inventory NetBox serves as our asset inventory. We integrate the interaction with the CSAF matching system as well as the processing and tracking of the processing status of matches into NetBox as a plugin. By this means we facilitate the use of advisories for the operator’s operational security staff. We present initial results and discuss challenges we have encountered, e.g., different sources of asset information for the same asset, inconsistent or incomplete information in assets and/or CSAF documents, weighting of attributes during matching, and scalability of the approach.
Behind the Curtains of the Common Security Advisory Framework: A Critical OT Perspective
Christian Schroeder and Alex Steg (Siemens)
After three years of building a service for vulnerability management in operational technology environments (OT) that consumes CSAFs, it is time to reflect on the journey. On the surface, CSAF promises standardization, automation, and improved transparency. But what happens when we look behind the curtains? Our presentation offers a critical examination of CSAF from an OT standpoint, highlighting the gaps between its promise and its practical implementation by publishers. While CSAF streamlines security operations in standardized IT environments, its adoption in OT landscapes reveals challenges that go beyond the current scope of CSAF: contextual relevance, vendor alignment, and discoverability. Let’s have a look at the real-world applicability of structured advisories in complex industrial ecosystems. We invite you to join us as we share field insights and explore what needs to change for OT Vulnerability Management to fully leverage CSAF not just in theory, but in practice. The session will feature practical examples based on real-world CSAF advisories from industrial vendors and will reflect on how these advisories are consumed by one of the first OT cybersecurity tools to actively leverage CSAF for vulnerability management and asset risk assessment.
CSAF & AI
Sonny van Lingen (Huawei)
Lunch
CSAF for Cloud Native? Challenges and a Proposal
Christoph Plutte (Ericsson)
A modern, cloud native microservice based application typically consists of multiple microservices where each microservice consists of other services and multiple container images which again contain multiple components or software libraries. Given a software vulnerability in a library present in several different container images of the application, how best to describe this situation in CSAF? CSAF provides concepts to describe complex products containing multiple sub-components and each of these sub-components can be linked separately to a vulnerability. However, we argue that the support in CSAF for describing relationships between products and components is limited and not ideal for modern cloud-native microservice based applications leading to suboptimal readability and ambiguities. To make CSAF fit for cloud native applications, we propose to introduce a third core concept besides products and vulnerabilities that we call “occurrence”. We describe key features of the occurrence concept and give detailed examples. We believe that introducing a separate concept for occurrences of vulnerabilities in products not only greatly improves the applicability of CSAF for cloud native applications, but also opens up new use cases such as describing scan reports from vulnerability analysis scanners in CSAF as a common standard across various vendors.
Visions for CSAF - Challenges and Perspectives (Panel)
Networking Break with Afternoon Tea
CSAF beyond Security
Florian Gilcher (Ferrous System)
As the name implies, CSAF comes out of the security space. However, it has usefulness beyond just those environments. In this talk, we’re going to present how we plan to adopt and deploy CSAF for so-called “management of known issues”, a manual and non-automated practice in safety critical environments. In this talk, we argue that CSAF is a already great tool for all kinds of high-assurance software and an important connecting piece. We also argue that CSAF has potential for future open-source businesses adressing high assurance needs
Closing Remarks

What's Included
in your CSAF Community Days Experience
Your registration grants you full access to an exceptional two-day program designed to maximize learning, networking, and collaboration:
Comprehensive Conference Program - Engage with cutting-edge presentations, panel discussions, and technical sessions led by CSAF practitioners, implementers, and industry experts. Stay tuned – detailed conference program will be published shortly.
Full Catering Throughout Both Days - Stay energized with complimentary coffee, tea, and refreshments during breaks, plus delicious lunch served each day to fuel your networking and learning.
Exclusive Evening Reception & Dinner - Join fellow attendees at the Südwestpark Hotel for an evening of networking and exchange. Enjoy a welcoming reception, dinner buffet, and beverages in a relaxed atmosphere - the perfect opportunity to connect with the CSAF community and forge lasting professional relationships.
Ticket classes
CSAF Community Days
Regular
Onsite Ticket
(valid from November 1st, 2025)
349,00 €
plus VAT
Shopping cart
BS150: CSAF Community Days
was added to the shopping cart.
CSAF Workshops | 10.-12.11.2025
Get informed and register now!
From 10 to 12 November 2025, OASIS is hosting practical workshops on the Common Security Advisory Framework (CSAF) in Nuremberg.
These workshops provide a unique opportunity to delve deeply into the creation, management, and dissemination of security information.
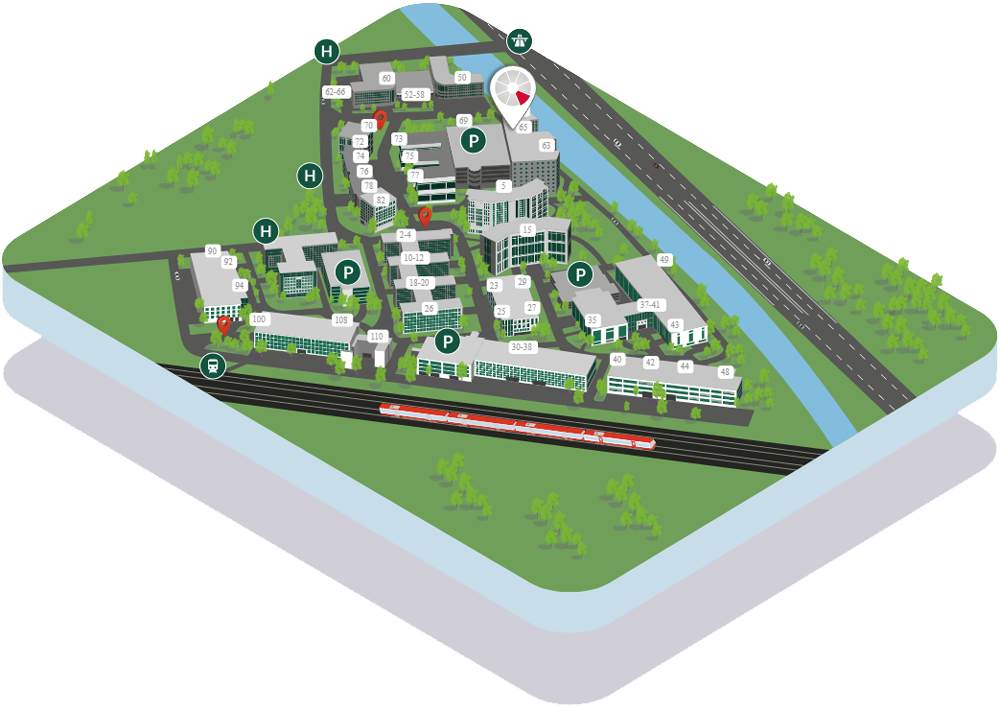
Location:
qSkills™ GmbH & Co. KG
Südwestpark 65
90449 Nuremberg
Germany